Ronin Network - Rekt II

The Ronin Network bridge was exploited for roughly $12 million, due to a critical oversight in a contract upgrade.
For the Axie Infinity community and Ronin Network users, the words "bridge exploit" likely trigger PTSD.
After the monumental $624 million hack in March 2022, many hoped those days were behind them.
But on August 6, those old wounds were reopened as Ronin faced yet another attack.
This time the damage was significantly less, but the psychological impact resonates deeply.
It's as if the crypto world is watching a horror movie sequel, wondering if the protagonist has learned from past mistakes or if they're doomed to repeat them.
As Ronin stumbles yet again, we're left wondering, how many wake-up calls does a project need before it finally masters the basics of operational security?

Credit: Chaofan Shou, Ronin Network, Verichains
Just when you thought it was safe to cross the Ronin bridge again, history repeats itself in a smaller, yet equally alarming fashion.
On August 6, the Ronin Network, still wearing the crown for the largest hack in crypto history, stumbled into another exploit.
This time, the damage was $12 million, a far cry from the $624 million heist of 2022, but no less embarrassing for a project that should have learned its lesson.
It's as if the Ronin team decided to reboot their horror franchise with a low-budget sequel that nobody asked for.
As the saying goes, "Fool me once, shame on you. Fool me twice, shame on me."
But what do we say when a project gets fooled twice by similar oversights?
Perhaps it's time for a new adage: "Hack me once, shame on the attacker. Hack me twice, shame on my operational security."
Like a digital Paul Revere, Chaofan Shou was the first to sound the alarm on X, alerting everyone that once again, the Ronin bridge was under attack.
Unlike their previous six-day delayed reaction, this time Ronin was a little quicker on the draw.
Psycheout.ron, COO of Ronin, responded shortly after the exploit was detected.
"The Ronin Network bridge has been paused while we investigate a report from whitehats about a potential MEV exploit. The bridge currently secures over $850M which is safe."
Approximately three hours later, the official Ronin Network account confirmed the exploit, stating that white hats had alerted them and the bridge was paused 40 minutes after the first on-chain action was spotted.
They revealed that the attackers had withdrawn just under 4K ETH and 2M USDC, valued at around $12M, which was the maximum single transaction withdrawal limit, a safeguard that prevented further damage.
As with many crypto heists, the devil was in the details, or in this case, in the upgrade process.
Verichains highlighted the root cause of this exploit, a failure to properly initialize a critical parameter during a contract upgrade. Following is how it unfolded.
The Fateful Upgrade: On August 6, the Ronin team deployed an update to their bridge manager, moving from version 2 to 4.
This upgrade introduced a new implementation contract, MainchainGatewayV3, which was deployed just 6 days prior.
The Ronin upgrade hub shows the changes in this new implementation, including modifications to how the contract handles operator weights and withdrawal submissions.
The Critical Oversight: In their haste, they called the initializeV4 function but neglected to call initializeV3. This seemingly minor oversight would prove costly.
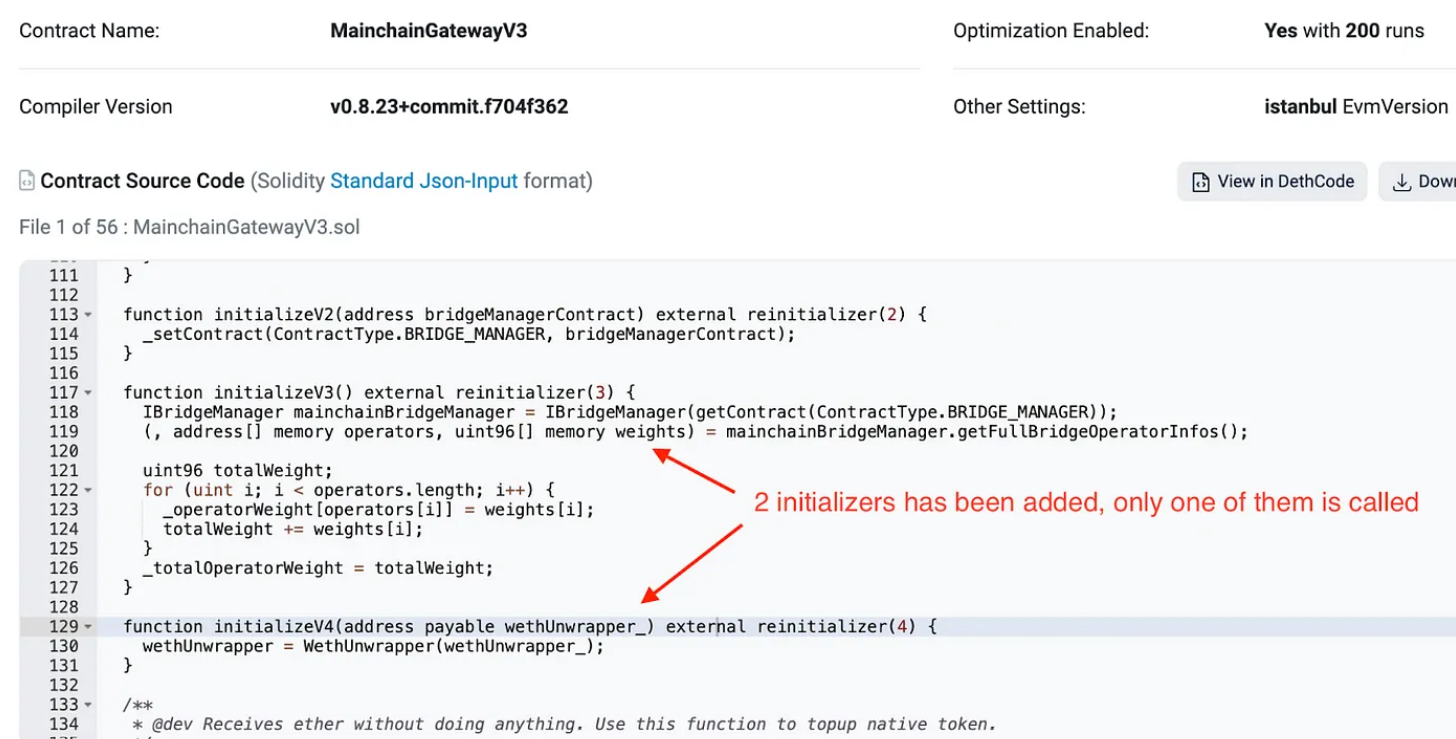
The Unintended Consequence: The _totalOperatorWeight variable was left uninitialized, defaulting to zero. This meant that the minimumVoteWeight parameter, crucial for cross-chain verification, was effectively disabled.
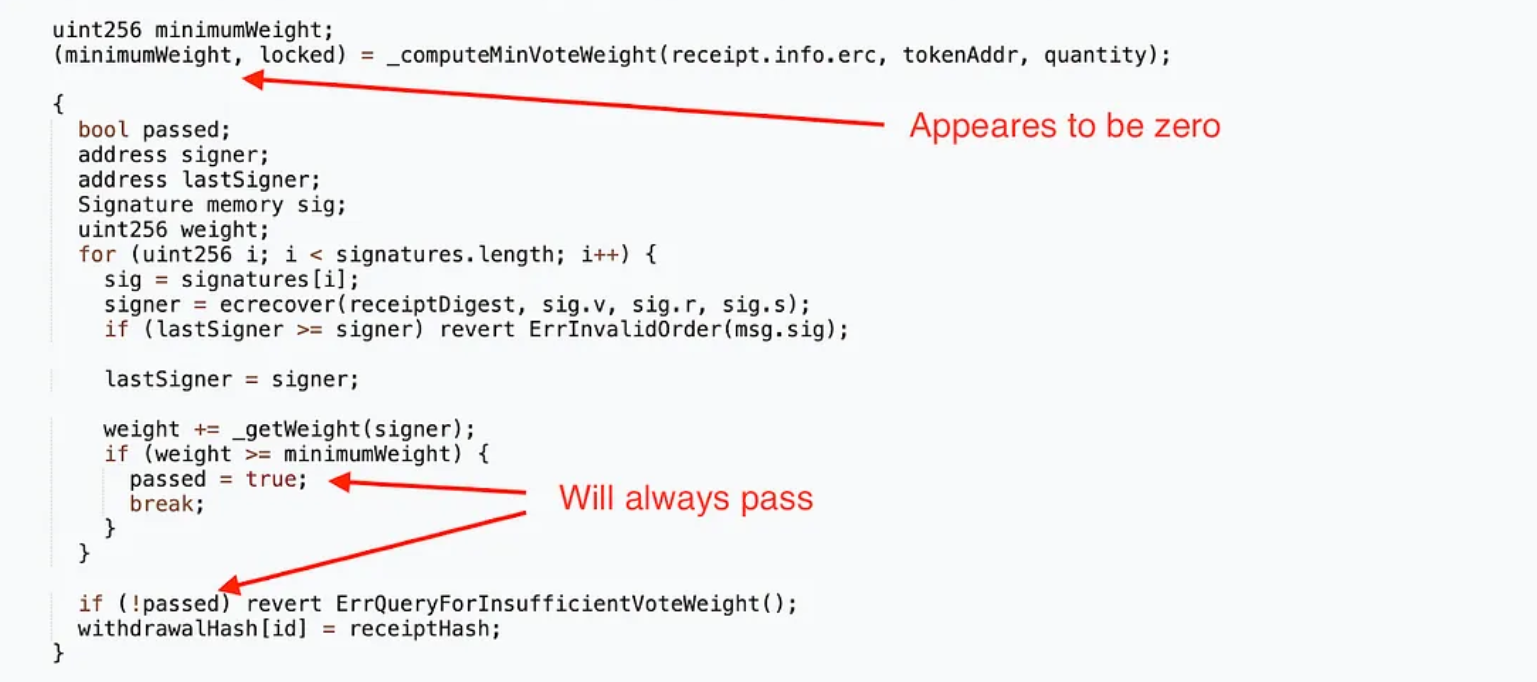
The Exploit: With security checks effectively disabled, the vulnerability was ripe for exploitation. An MEV bot identified the vulnerability and front-ran any potential manual exploit attempts, executing the attack and directing the funds to its own address.
The Damage Control: Thanks to a daily withdrawal limit, an additional $72 million was saved from being pilfered. The Ronin team managed to pause the contract about 38 minutes after the exploit began.
In a surprising turn of events, the stolen funds were swiftly returned, thanks to lightning-fast MEV white hats who outpaced potential malicious actors.
The ETH, valued at approximately $10 million, was promptly sent back to the Ronin team.
The remaining USDC was returned shortly after.
In recognition of their vigilance and integrity, the Ronin team announced a $500,000 bounty for the white hat hackers involved.
Ronin also stated that the bridge will undergo an audit before reopening, with Ronin aiming to shift its operation away from the current structure.
A post-mortem is scheduled for next week, promising deeper insights into the technical details and planned preventive measures.
This incident highlights the double-edged sword of upgradeable contracts and the critical importance of meticulous implementation.
Ronin's oversight turned a routine upgrade into a $12 million lesson in humility.
How many more wake-up calls can a project survive before users decide it's time to cross a different bridge?

Despite their improved response time, Ronin's failure to properly implement and test their latest upgrade reveals a project still stumbling over basic security practices.
They dodged a bullet thanks to the fortuitous intervention of MEV white hats, but luck isn't a sustainable security strategy.
For a project that's already suffered the largest hack in crypto history, this near-miss should be a final wake-up call.
It's time to prioritize rigorous security measures over hasty upgrades.
Moving forward, Ronin and indeed all blockchain projects should do the following:
-
Always implement thorough tests for contract upgrades.
-
Collaborate with auditors to verify correct deployment.
-
Be cautious with the Initializable contract from OpenZeppelin, understanding its potential pitfalls.
Ronin Network wobbles precariously between redemption and infamy.
In an ecosystem where reputation is as volatile as the assets it secures, how many near-misses can a project survive before users decide to seek safer shores?

REKT serves as a public platform for anonymous authors, we take no responsibility for the views or content hosted on REKT.
donate (ETH / ERC20): 0x3C5c2F4bCeC51a36494682f91Dbc6cA7c63B514C
disclaimer:
REKT is not responsible or liable in any manner for any Content posted on our Website or in connection with our Services, whether posted or caused by ANON Author of our Website, or by REKT. Although we provide rules for Anon Author conduct and postings, we do not control and are not responsible for what Anon Author post, transmit or share on our Website or Services, and are not responsible for any offensive, inappropriate, obscene, unlawful or otherwise objectionable content you may encounter on our Website or Services. REKT is not responsible for the conduct, whether online or offline, of any user of our Website or Services.
